Easy way to enforce and test Least Privilege AWS IAM Policy
It is hard to count how many times I saw companies grant AdministratorAccess to developers and partners. I know you trust them, but...
It is hard to count how many times I saw companies grant AdministratorAccess to developers and partners. I know you trust them, but give them PowerUserAccess instead. It is a small change but essential for your security. It provides full access to AWS services and resources but does not allow management of Users and groups. That's it. No more random users created for a friend or non-technical persons because they wanted to check out something. Need access? Get it with permission from the real administrator.
Nevertheless, I wanted to show you how to determine the least privileged privilege in your case. If you already know it and apply granular access - excellent! Keep doing it. But what if you don't? What if you have IAM roles or IAM users created a while ago with too unrestrictive access, and now it is hard to say what is needed? No worries, it is easy to do.
1) Log into the AWS console and open "Identity and Access Management (IAM)".
2) Under "Access management" click on Users or Roles, and then find the one you want to restrict. In this example, we use a "terraform" user.
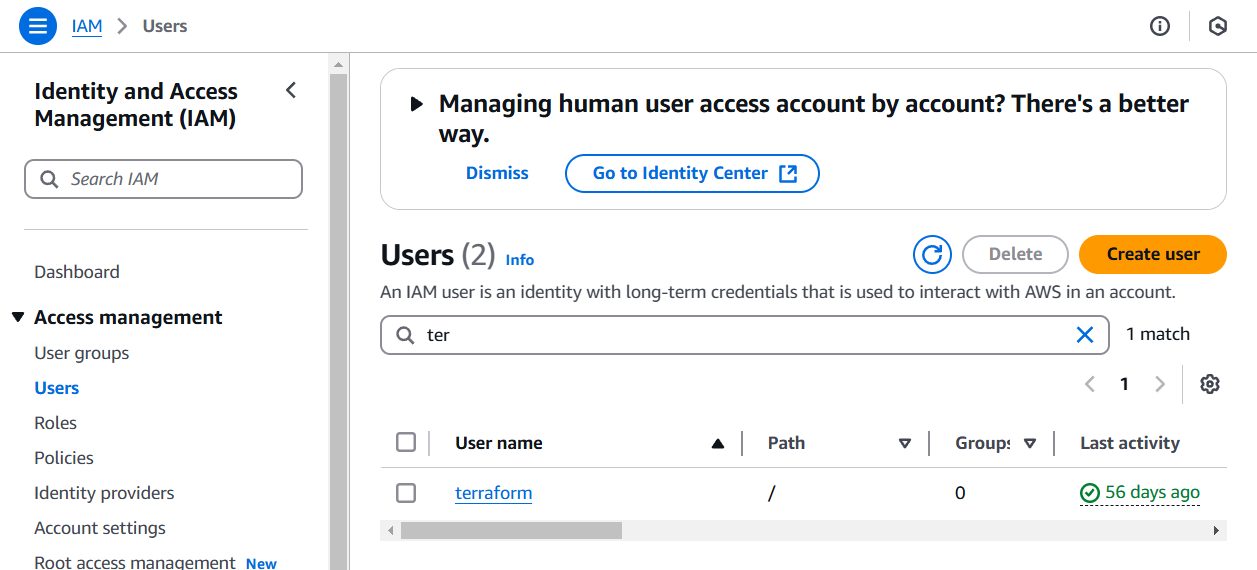
3) Click on the user. Scroll down to "Generate policy based on CloudTrail events". Click the "Generate policy" button.
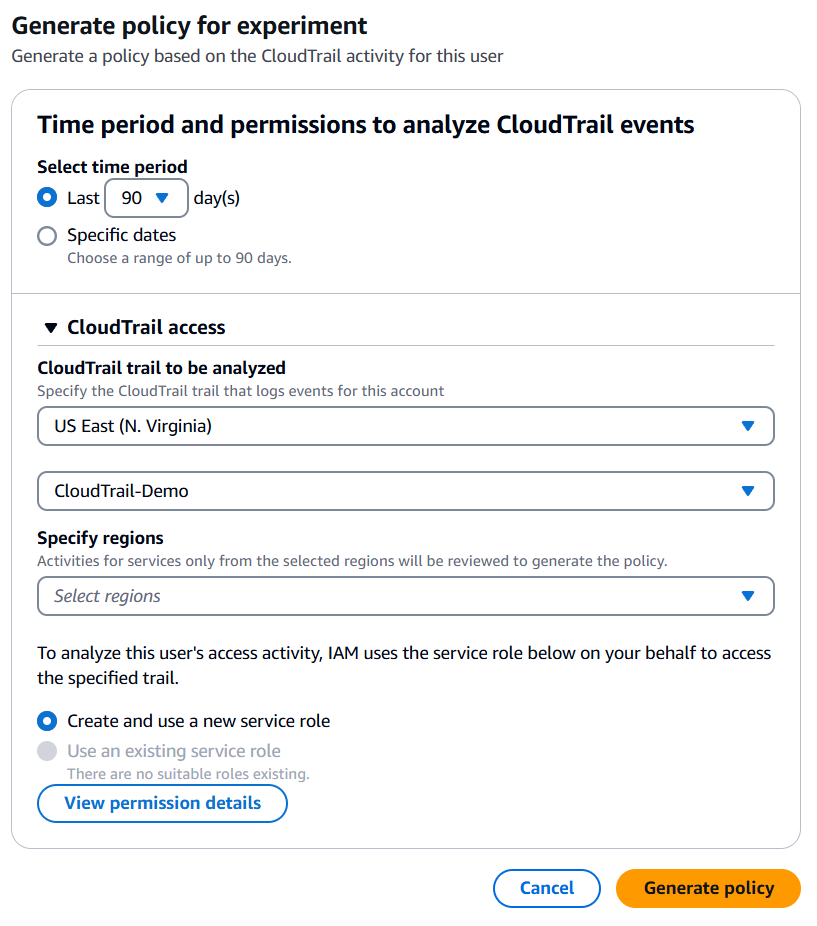
4) Pick the period to analyze the activity of the user. You can select up to 90 days.
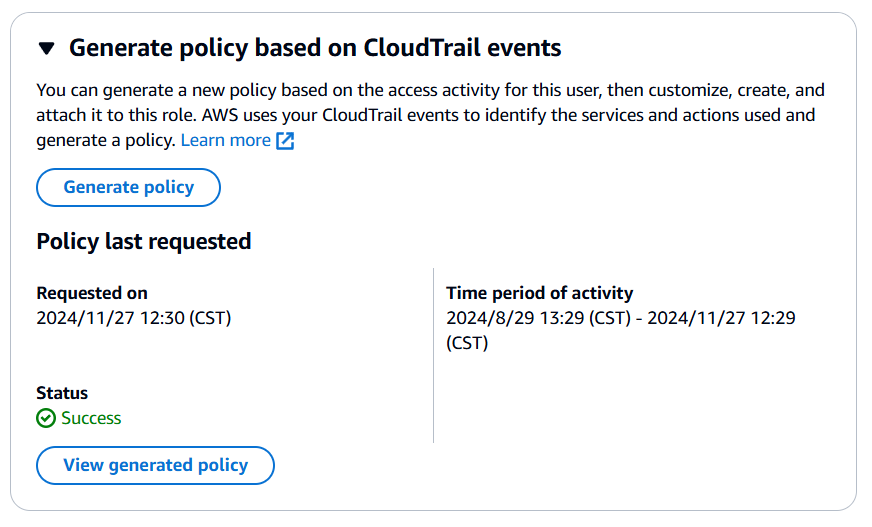
5) Click on "Generate policy". This may take up to 30 seconds. Do not refresh the page or leave the page. You will see the "View generated policy" button when the activity is completed. Click on it.
6) Review the new policy on the following two screens and click "Next". On the last one, click "Create and attach policy".
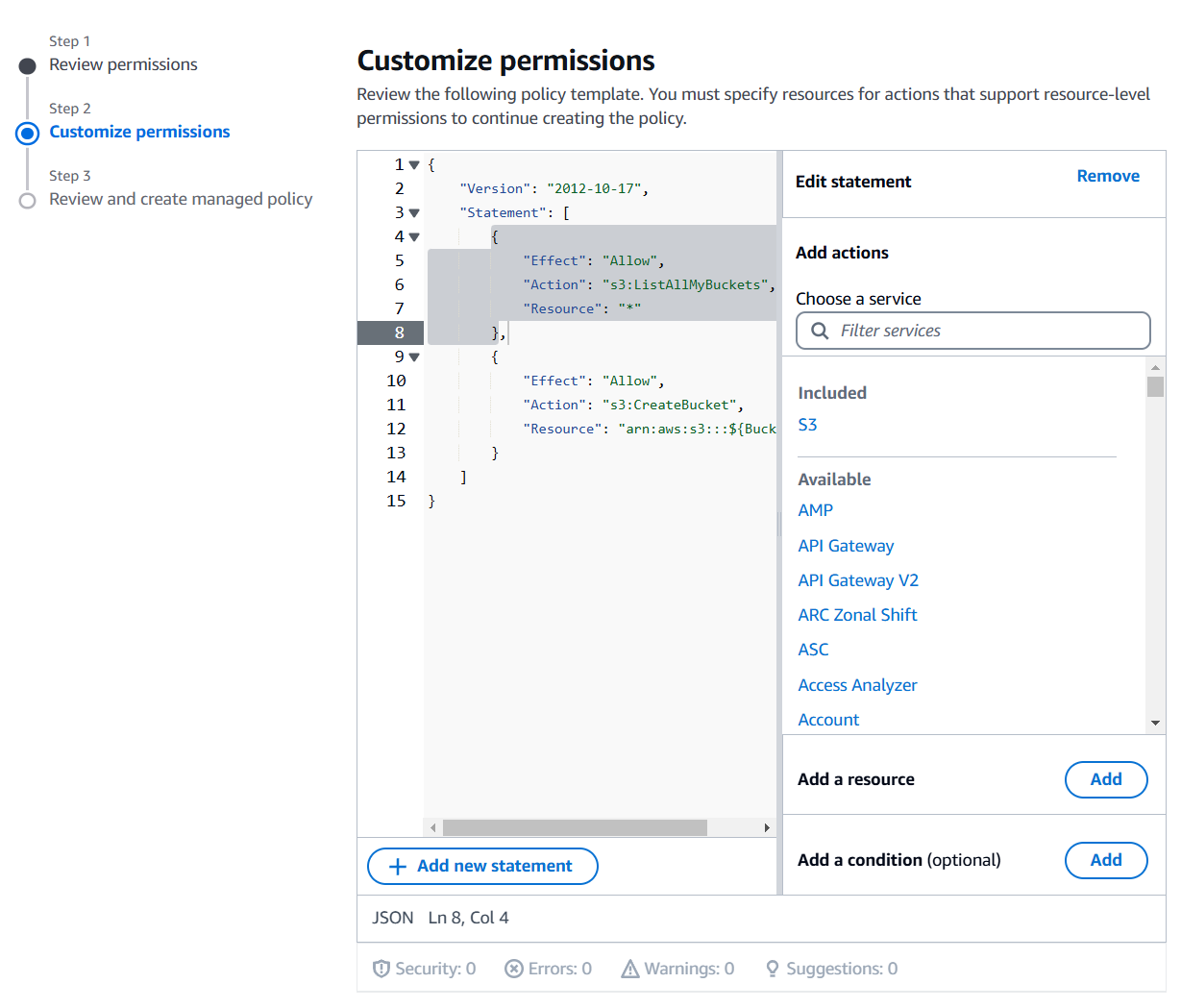
7) Note that the new policy is attached to the user. Select and remove the previous policies if they are no longer needed.
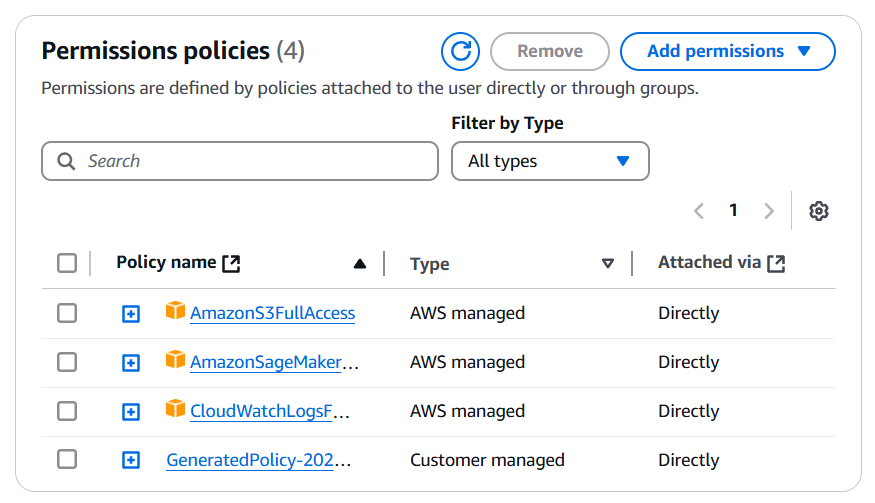
Now, you have a user with the least privileged access. In most cases, no further changes will be needed. However, if the user sometimes performs an action that was not done during the last 90 days, such as password rotation or anything else that is done extremely rare, it will fail. So keep an eye on the user until you are 100% confident that no required permission is missing.
Testing IAM Policy
Sometimes, you know that the IAM user or IAM role must perform an action, but you are still unsure if that is allowed. There could be multiple reasons why it is denied despite the permission being granted in the policy because the final permission is determined as a combination of
- Identity-based policies
- IAM permissions boundaries
- AWS Organizations service control policies (SCPs)
- Resource-based policies
For such cases, AWS offers an IAM Policy Simulator, where you can find your answer almost instantly. For example, if you want to know if "iam:CreateRole" is allowed, run the following AWS CLI command
aws iam simulate-principal-policy --policy-source-arn <POLICY_ARN> --action-names iam:CreateRoleThe output will show you why it is allowed or denied.
"EvaluationResults": [
{
"EvalActionName": "iam:CreateRole",
"EvalResourceName": "*",
"EvalDecision": "implicitDeny",
"MatchedStatements": [],
"MissingContextValues": []
}
]Easy. Right?
Looking for help? Reach me any time.